Apple AirTag Trackers Already Hacked And Reprogrammed By Security Researchers
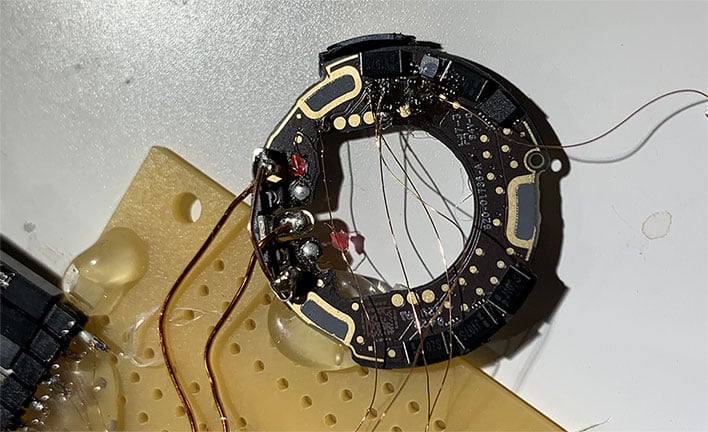
Well, that was incredibly fast. Apple released its AirTag trackers to retail less than two weeks ago, and someone has already hacked the tiny gadget. Security researcher Thomas Roth did the deed, as he managed to crack into the microcontroller and re-flash it with his own custom firmware, essentially resulting in a jailbroken AirTag.
The tiny devices are clever and affordable ways of keeping track of items you really do not want to lose. They sell for $29 a pop (or $99 for a four-pack), and provide a private and secure way of finding lost items by leveraging Apple's immense Find My ecosystem. Users can see a lost item's last known location on a map, then when they are within Bluetooth range, they can have the AirTag play a sound.
There are stalking concerns associated with AirTags and how well they work. Apple took this into consideration by alerting users to nearby trackers that are not their own and pushing a notification to their handset. However, the way AirTags are currently configured, the audible alarm only sounds after three days. Additionally, Android users do not get the benefit of a notification like iPhone users do.
The apparent ability to jailbreak an AirTag potentially exacerbates security and privacy concerns, though it does not sound like this is something that is particularly easy to do. Roth noted that he busted a pair of AirTags before finally being successful.
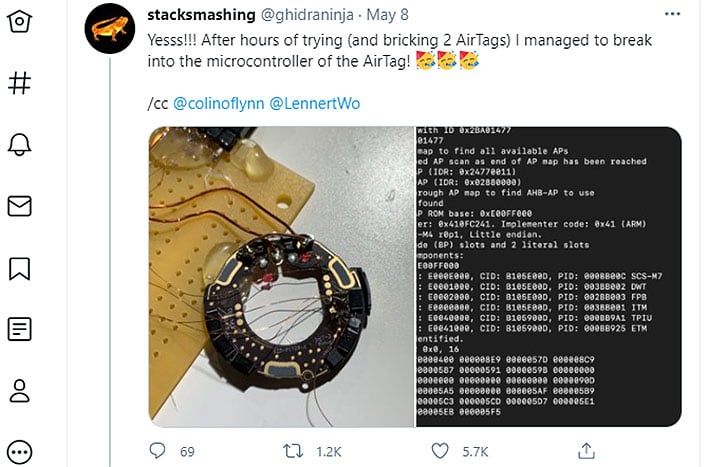
"Yesss!!! After hours of trying (and bricking 2 AirTags) I managed to break into the microcontroller of the AirTag," Roth wrote on Twitter.
Roth flashed the firmware and then posted a short clip showing one potential use—he modified the NFC address for Lost Mode so that when he hovered his iPhone over the hacked tracker, it opened his own website rather than the Find My website like an unaltered AirTag would.
It's easy to see how this could be used in nefarious ways, like sending a user to a phishing site that is made to look like an official Apple portal. From there, a hacker could steal an unwitting person's details, depending on how convincing the site is, and the level of tech savvy on behalf of the victim.
Let's not make a mountain out of a molehill, though. A hyper-motivated hacker would first need to get their mitts on someone's AirTag, then successfully hack it (no easy task, apparently), and place it back where they took it, all without getting caught. And after all that, they would need the user to lose their item, find it, and fall for the phishing scam.
It's not an efficient approach to phishing, not like Covid-19 phishing emails. On the flip side, though, a modder could leverage this for their own benefit, by having the tracker open up an app of their choice or some other use.