Google says it has fixed a major Chrome OS bug that locked users out of their devices. Google's bulletin says that Chrome OS version 91.0.4472.165, which was briefly available this week, renders users unable to log in to their devices, essentially bricking them.
Chrome OS automatically downloads updates and switches to the new version after a reboot, so users who reboot their devices are suddenly locked out them. The go-to advice while this broken update is out there is to not reboot.
The bulletin says that a new build, version 91.0.4472.167, is rolling out now to fix the issue, but it could take a "few days" to hit everyone. Users affected by the bad update can either wait for the device to update again or "powerwash" their device—meaning wipe all the local data—to get logged in. Chrome OS is primarily cloud-based, so if you're not doing something advanced like running Linux apps, this solution presents less of an inconvenience than it would on other operating systems. Still, some users are complaining about lost data.
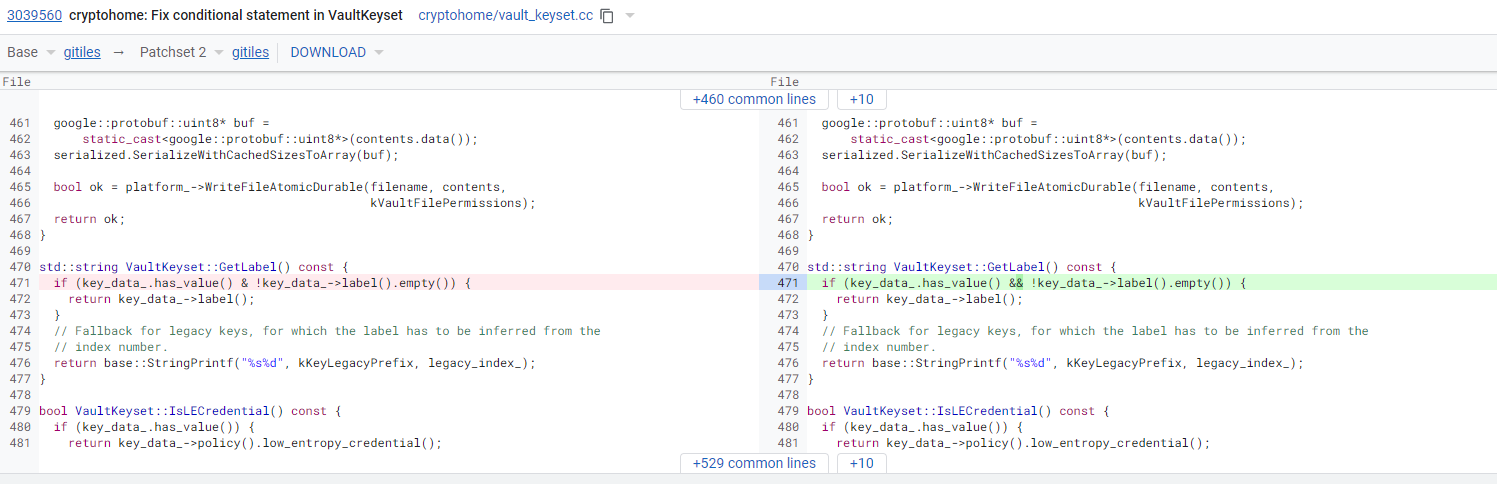
ChromeOS is open source, so we can get a bit more detail about the fix thanks to Android Police hunting down a Reddit comment from user elitist_ferret. The problem apparently boils down to a single-character typo. Google flubbed a conditional statement in Chrome OS's Cryptohome VaultKeyset, the part of the OS that holds user encryption keys. The line should read "if (key_data_.has_value() && !key_data_->label().empty()) {" but instead of "&&"—the C++ version of the "AND" operator—the bad update used a single ampersand, breaking the second half of the conditional statement.


 Loading comments...
Loading comments...
